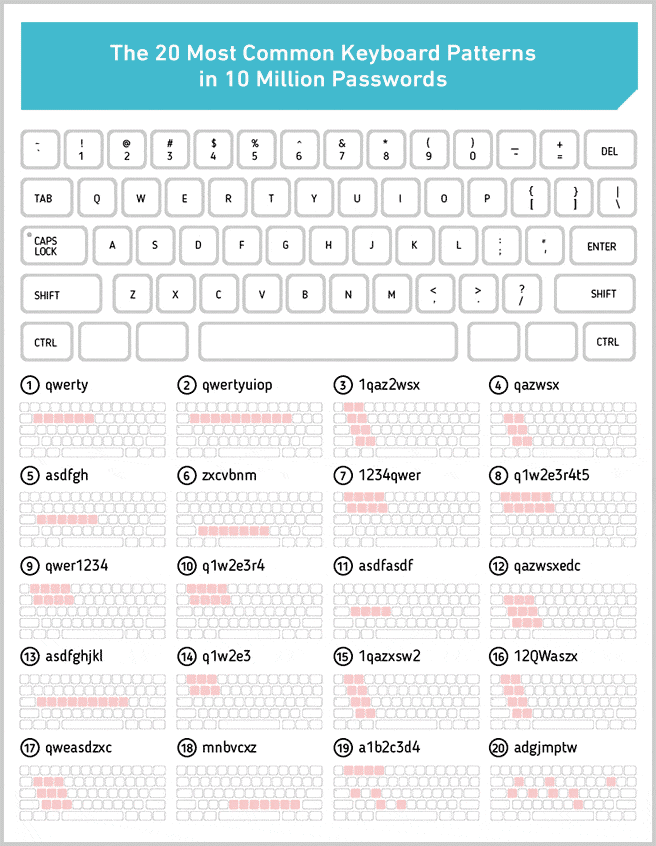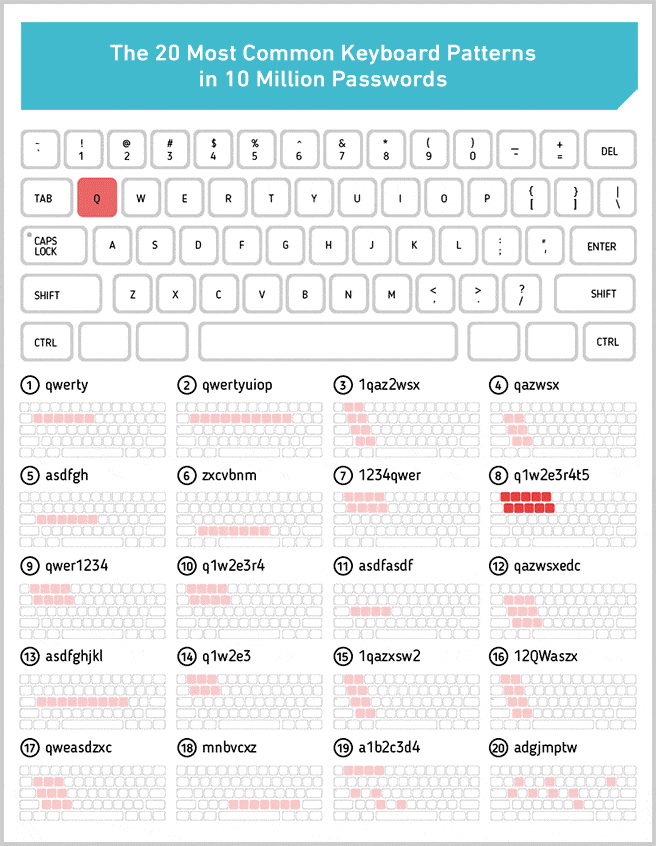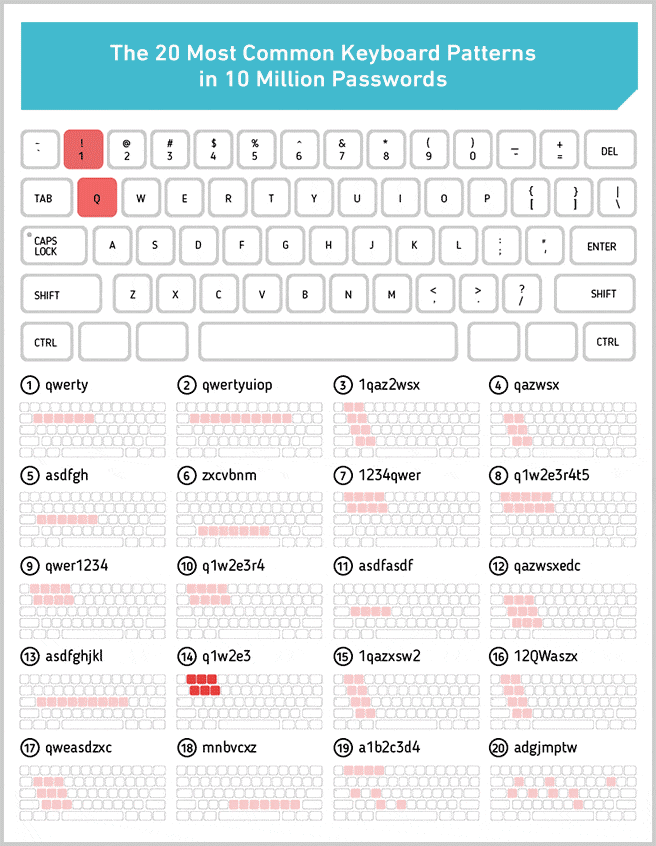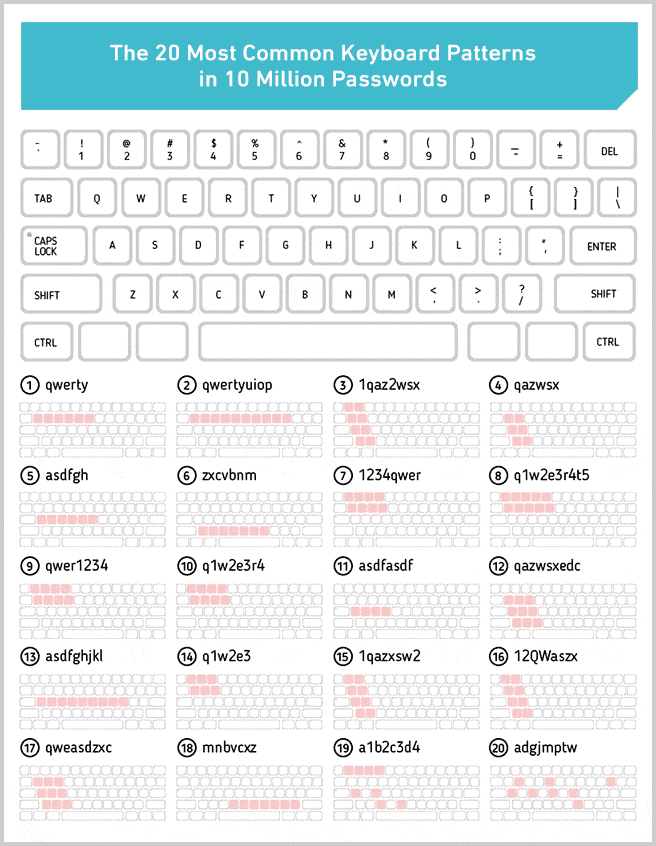
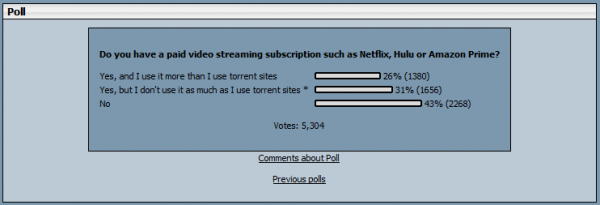
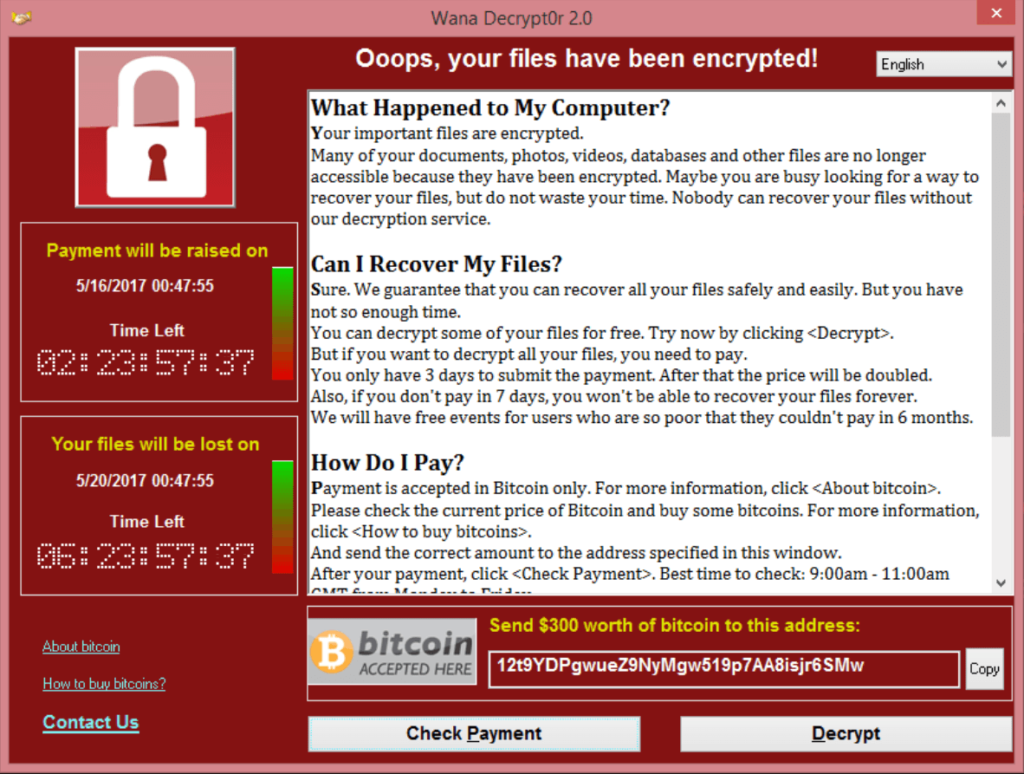
Can a VPN prevent my data being harvested?
Posted 23rd August, 2018 @ 12:21 pm | by Neil Cumins | inGuides
Data harvesting has taken centre stage in recent months, from Facebook’s ongoing travails to high-profile leaks involving firms like Yahoo and Equifax.
As consumers lose enthusiasm for volunteering intimate details of their lives to faceless marketing companies, data harvesting has become a popular topic of discussion.
Most people now appreciate social media platforms, web browsers and search engines spy on every keystroke and page view, looking for information they can sell to third-party agencies.
But do VPNs provide greater privacy, or are they something of a fig-leaf?
Do VPNs prevent personal data harvesting?
The simple answer is – it depends what you’re doing.
A VPN is great for passively consuming content without letting the world and its appointed ad agency know where you’ve been.
However, anonymous browsing only takes you so far.
If you log into a website – which you’ll need to for gated content and ecommerce portals – you’re still generating activity logs.
A VPN is therefore only beneficial when browsing websites as an unregistered guest, such as watching publicly accessible media streams or looking at archived Reddit threads.
Logging into an account won’t be picked up by the VPN, but that website will track your activity even if you’ve accessed it via a securely encrypted tunnel protocol.
Similarly, it’s possible to conduct searches in Google and Bing through a VPN without leaving an electronic footprint.
But you’ll need to be logged out of any accounts, which means access to Google Docs and YouTube histories won’t be possible.
As soon as you log in, everything you do is monitored through your account rather than your web browser.
And once Google knows you like using VPNs, it’ll start displaying adverts for VPN providers – ironic, but inevitable.
Once more unto the breach
At least using a VPN prevents data harvesting by criminals.
Even a mediocre hacker could eavesdrop on someone sitting in a café, once their phone or laptop is logged into the free WiFi network.
Conversely, a VPN creates an encrypted connection between host and recipient devices, ideally using uncrackable 256-bit encryption keys and advanced authentication certificates.
This is particularly advantageous when seeking to avoid geolocation settings, such as the ones used to block local radio stations or live sporting events.
Logging an enquiry
Another issue with data protection centres on the moral ambiguity of VPN services keeping user logs.
We recently revealed how a href=https:// vpns.co.uk/can-i-trust-my-vpn-not-to-spy-on-me a quarter of VPN providers were collecting log files on users, potentially enabling the identification of individual users.
This data could then be resold, used to identify users prior to criminal proceedings, or simply left in a ‘secure’ data centre for an unspecified time period.
Avoid VPN products from companies who claim they need to retain Personally Identifiable Information, or who collect ‘anonymous’ data about site visits.
Read consumer reviews, choose uncapped (or unlimited) VPN packages, and scrutinise the VPN’s privacy policy for a definitive guarantee no logs will ever be made or retained.